Background
Some time it is important to intercept and inspect network calls that are being made from your android device. Specially of you have made an android app want to debug the outgoing network calls. In a browser it is very simple , you simply right click and then inspect element. Network tab will give you the network calls made with the details. Each browser has their own native inspector. I generally use
firebug in my firefox. But as I was saying this is not possible in android devices. So we have to divert all device network calls via a proxy and inspect our calls there. For this demo I am going to use
Fiddler as a proxy.
Getting started
You can download and install Fiddler web proxy from
here.
After installing it go ahead and start it up. You should see following screen -
Note : You can use shortcut Ctrl + X shortcut to clear the captured network data.
Lets set up some settings so that we can use this as a proxy for out android device.
Go to Tools -> Fiddler Options . Navigate to Connections tab and select "Allow Remote computers to connect" option.
After you select this you will see an alert stating that remote connection network traffic will bounce via your computer. Select OK.
Note1 : You will have to restart Fiddler for changes to take effect.
Note2 : After selecting Accept Remote connections restart fiddler. In case windows firewall prompts you to allow access, check all three checkboxes and click the Allow Access button
Just to make sure your Fiddler web proxy is up and running you can type "localhost:8888" in your browser and Fiddler echo service should respond back 200 status.
If you don not want to inspect and decrypt https connection skip to Configuring Client section.
Decrypting HTTPS Connections
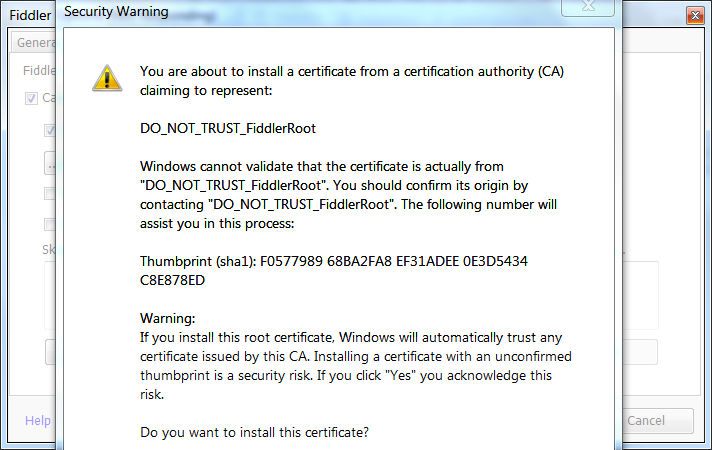
If you want to intercept and decrypt https (SSL) traffic as well. You can again go in Tools -> Fiddler Options. This time navigate to "HTTPS" tab and select "Decrypt HTTS traffic". You will get a prompt to trust a root CA certificate fiddle provides. For now select "No". Will explain why in some time.
Even if you press yes next window should warn you again.
Take the hint. It's not safe :) Atleast there is no need for us. We will see why in below section.
You need to add this certificate in list of trusted certificates in your Android device. I will show that in the end of configuring Client section.
What is this CA ROOT certificate that we have to trust and how is it related to HTTPS traffic decryption?
This section is not really required for testing network traffic. I am just adding for people who are interested in understanding the concept. Others can skip this section.
Whenever https is enabled on a server container like apache tomcat you need to do some SSL configurations. Important thing to provide to the server is the keystore which stores the certificate that the private keys. When any client connects to this server, server provides a copy of the SSL certificate to the client. Now client (Android device in our case) has something called a trust store that which has certificates that the client can trust. If the client does not trust the certificate server has provided then connection errors out. There certificate are typically generated and provided by know certificate providers like Digi Cert, Go Daddy etc. For more information on Certificate providers read the Wiki -
What happens in Fiddler is as follows - Client makes an https call. Fiddler intercepts it and forwards it to the actual server. When it gets a response Fiddler uses it's own certificate and forwards the response to the client. Why? Think if Fiddler forwarded the request directly yo the client. Whatever client sends in subsequent https connection will be signed with the public key that can only be decrypted by the server that has it's private key which in this case will be the mail site server where request is sent. Since Fiddle does not have that Fiddler sends it's own certificate to the client. Client signs subsequent data with that certificates public key and since Fiddle has this certificate (with it's private key) it can decrypt it.
Wow that a security hazard? Well it a well known attack actually. Also called
man-in-the-middle (Read Wiki on it) attack. Do not worry about it. Your client should trust that certificate in order for it to work.
So why we did not accept the certificate to trust? Because this on the machine which hosts the Fiddler and we want to intercept the calls from our Android device. So Android device is the client and not the machine that hosts Fiddler. You can accept the certificate as trusted one in your android device. As a test if you go on any https site (on your machine) now you will get the unstrusted certificate warning. Do not accept and proceed :)
After this is your Fiddler is all set to Intercept your calls. All you have to do is configure the client (your android device) to use this as the proxy.
Configuring the client (Android device)
Long tap on your Wifi (Note your machine where Fiddler is running and the Android device should be on the same wifi network). Click on "Show Advance options".
Select Manual as the proxy type. Put in proxy hostname as your machines IP address. Change the port to 8888 which Fiddler runs on by default.
Let every other setting be as it is.
You can then see captured data in the Fiddler. I tried a simple http site -
http://moma.org
Lets try an https site now.
https://google.com
Opps what happened? Well we have not added fiddlers certificate to the list of trusted certificate list on device yet. Lets do that now. Again this is only for decrypting https data. Skip below for http connections -
In your browser of android device go to following URL -
You will get the prompt to install certificate. Provide some certificate name. Choose "Wifi" in the credentials Use section and click Ok. Https connections should work now.
Note : Fiddler should be running for this.
After you install the certificate. Typically you should see a toast that says certificate installed -
Don't mind my delay in taking above screenshot :) The toast is almost faded. Anyway after this you should see a notification on your device saying your network activity is monitored -
and when you click on "Check trusted credential" you can see the user installed cert on your system -
After you are done testing you can remote the cert from here. tap on the cert entry and you should see new activity with cert info. Scroll to the bottom and click Remove to remove this cert from your system. Do not forget to remove manual proxy and all goes back to normal :)
Resolving “enter the password for credential storage” issue?
Note if you have trouble installing certificate as I was (i was continuously getting following prompt).
then remove all security you have for lock screen - I had pattern. Now try installing the certificate again. You will get prompt to add lock security - password or pin.
Go ahead and set it up. Then certificate should get installed.
Important Note : This is a good tool to analyze your devices network data but can be misused if you do not know what are you up to. So don't try this on your personal device with sensitive data . Probably try on emulator first or a test device. I don't take any responsibility for any testing that you do using information in this post!
Related Links